Don’t confuse the hacking of a digital exchange with that of a blockchain. Although a common mistake, these are two very different things. Blockchains are decentralised. Digital exchanges are not. So, what exactly makes a Blockchain impervious to hacks?
Protocols: Open-sourced and Decentralised
Blockchains, the technology behind most cryptocurrencies, are built on open-source protocols, which means they are public and transparent. These blockchains are distributed, or in plain English, spread out over a network of nodes or computers all around the globe and connected through the internet.
These protocols work on consensus mechanisms like proof of work (PoW) or proof of stake (PoS). These mechanisms protect the blockchain from attacks by hackers.
Since Blockchains are decentralised, their ledgers or blocks of transaction data, are visible and in full view of anyone with a computer, and there is no central location that can be attacked.
This architecture ensures the nodes must cooperate in order to verify every transaction before it is committed to the blockchain. Bitcoin for example, must have a consensus of the majority of nodes in the network verifying a transaction before it is committed. So, a minimum of 51% of all nodes in the network must be in agreement for data to be included in each new block of the chain.
So, if there is an attack on one node in the network, where transaction data is illicitly altered, this node would simply be rejected by the majority of nodes in the network. This is the first layer of security.
Hashing Algorithm
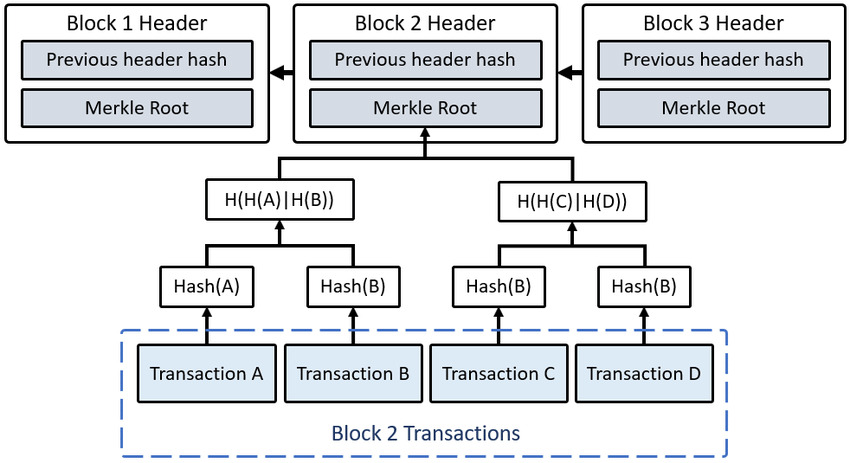
So, let’s take a closer look at these blocks of transaction data in the chain. When one block of transaction data is full, it is added to the chain and a new block is born. This block is then run through a hashing algorithm, or cryptographic function, that compresses it. Bitcoin uses the double SHA-256 hash function compressing data into a 256-bit hash.
This hash is then used to seed the next block of data. In this way, each block in the chain is linked to the one on either side of it. And that is the very genius of it. If you alter any data in any historical block from earlier in the chain, then every subsequent block will be altered too. This, of course, means we can pinpoint which transaction data was altered. This is the second layer of security.
Are 51% Attacks Possible?
The simple answer is yes. But, they are improbable. The longer a blockchain is in existence, and the more users and nodes it has on the network, the less likely it is to be susceptible to this form of attack.
What is a 51% attack? In order for a hacker to successfully alter data in the blockchain, they would need the majority of nodes in the system to agree to their version of the blockchain. Therefore, they need to take control of 51% of the blockchain’s power.
This, of course, becomes prohibitively expensive at a certain point. This is why such a scenario would be virtually impossible for the likes of Bitcoin, the largest cryptocurrency network today. The market cap of Bitcoin alone is over $1 Trillion.
Likewise, a PoS based attack where a hacker would acquire a majority of all coins in a system such as that of Ethereum, the second largest blockchain network with a market cap of $68 Billion, is also highly unlikely. I’m not sure who would have that kind of money laying around. And if they did, you would need to pose the question; why would they intentionally devalue their own investment?
Has any Blockchain ever been Successfully Attacked?
Yes, 51% attack victims include Bitcoin Gold, Ethereum Classic, Electroneum, and recently, Grin. What have all of these blockchains in common? They all have a tiny number or nodes and miners securing their respective networks when compared to the top cryptocurrencies. Thus, they have lesser processing power, making it easier for an attacker to take control. From the thousands of coins in existence, some have only a handful of nodes in their networks. And of course, some giants like Bitcoin and Ethereum, have hundreds of thousands.
In summary, as the top cryptocurrencies grow ever more popular, their likelihood of falling victim to attack diminishes to zero.







